
A cybersecurity breach now costs companies an average of $4.4 million, according to IBM's 2025 Cost of a Data Breach Report. Yet many organizations still rely on firewalls designed to defend against threats from a decade ago.
Here's the situation: your firewall might check IP addresses and ports while attackers hide malware inside encrypted traffic and legitimate applications.
The gap between what traditional firewalls see and what modern threats exploit has never been wider.
We've spent years helping enterprises evaluate firewall architectures across Fortune 500 deployments and small business networks. This comparison cuts through vendor marketing to show you exactly how stateful, proxy, and next-generation firewalls actually work, and more importantly, which gaps each one leaves in your defenses.
You'll see real capability differences that matter when threats hit your network, not just feature lists from spec sheets.
What Firewalls Actually Do
A firewall is a network cybersecurity device or software designed to monitor and control incoming and outgoing network traffic in accordance with predefined security rules.
Its core purpose is to filter traffic between a trusted network (e.g., your internal LAN) and an untrusted network (e.g., the internet).
Historically, firewalls began as simple packet inspection filters that examined individual packets at the network and transport layers without tracking state.
Over time, firewalls evolved to include more intelligence and visibility. Understanding the types of firewall and their differences helps you select the right protection for your network's specific needs. With that foundation in place, we now turn to particular firewall types and what each brings.
Stateful Inspection Firewalls
Stateful inspection firewall tracks active connections as they pass through it. They remember the "state" of each network conversation and use this context to make smarter decisions.
How They Work
When a connection starts, the firewall records details in a state table. This table tracks the source, destination, port numbers, and connection status. For each new packet that arrives, the firewall checks if it belongs to an existing, legitimate connection.
This type of firewall operates at the network and transport layers (specifically layers 3 and 4 of the OSI model). They understand TCP connections and can distinguish between a new connection request and a response to an existing connection.
The Benefits
Stateful inspection offers several advantages over older packet filtering firewall methods. The firewall understands context, so it knows that a return packet from a web server is likely a response to a request your system made.
This approach runs fast and uses fewer resources than deeper inspection methods. The firewall makes quick decisions based on connection state and doesn't need to examine every byte of data inside packets.
Most networks today use stateful firewalls as a baseline. The technology matured over decades and has proven reliable for basic traffic filtering.
Where They Fall Short
Stateful firewalls don't look inside the application data itself. A hacker can hide malicious code inside legitimate-looking traffic, and a stateful firewall won't catch it.
These firewalls also struggle with encrypted traffic. Since they can't decrypt and inspect HTTPS connections, potential threats slip through undetected.
According to Google, approximately 95% of web browsing uses the encrypted HTTPS protocol, creating a massive blind spot for traditional firewalls.
Application-layer attacks, such as SQL injection or cross-site scripting, can pass through stateful firewalls. The firewall sees a normal web connection and allows it, unaware of the dangerous payload inside.
Proxy Firewalls
Proxy firewalls take a different approach. Instead of just inspecting malicious traffic, they actually intercept it. The proxy acts as a middleman between your users and the internet.
How They Operate
When a user requests to access a certain website, the request goes to the proxy firewall first. The proxy then makes a separate request to the website on behalf of the user. The website sends data back to the proxy, which inspects it before forwarding it to the user.
This creates two separate connections rather than a single direct connection. The external network server never communicates directly with your internal network. It only sees the proxy.
Proxy firewalls work at layer 7 of the application layer. They understand HTTP, FTP, SMTP, and other protocols.
Some proxies specialize in a specific application level gateway, while others support multiple protocols.
Security Advantages
Because proxy firewalls operate at the application layer, they inspect the actual content of communications. They read URLs, examine file attachments, and analyze application commands.
This deep packet inspection catches cyber threats that stateful firewalls miss. The proxy can block specific web pages, filter email attachments, and prevent data leaks by examining outbound traffic.
Proxy firewalls also hide your internal network structure. External systems never see your real IP addresses or know how many devices you have. They only communicate with the proxy.
Performance Trade-offs
All this inspection requires significant processing power. Proxy firewalls consume more resources than stateful firewalls and can introduce latency. Users might notice slower response times, especially during peak traffic periods.
Scaling proxy firewalls for large networks gets expensive. You need powerful hardware to handle thousands of simultaneous connections while performing deep inspection on each one.
Proxy firewalls work best when security trumps speed. High-security environments, such as financial and health institutions and government agencies, often accept a network performance hit for better protection.
Next-Generation Firewalls (NGFWs)
Next-generation firewalls combine the best of both worlds and add features that neither traditional stateful nor proxy firewalls offer on their own.
What Makes Them Different
NGFWs start with stateful inspection as a foundation, then layer on advanced capabilities.
They identify applications regardless of port or protocol. They recognize users, not just IP addresses. They detect and block threats in real time.
The term "next generation firewall" emerged around 2009 when Gartner defined specific requirements that went beyond traditional firewall capabilities. These network devices integrate multiple security functions into a single platform.
Core Features
- Intrusion Prevention Systems (IPS) actively monitor network traffic for suspicious patterns and known attack signatures. When the NGFW spots a threat, it blocks it immediately rather than just alerting you.
- Application awareness means the firewall knows the difference between Facebook and Salesforce, even if both use HTTPS on port 443. You create policies based on applications, not just ports and protocols. You might allow LinkedIn but block other social media, for example.
- SSL/TLS inspection solves the problem of encrypted traffic. NGFWs decrypt HTTPS traffic, inspect it for threats, then re-encrypt it before sending it along. This happens transparently to users.
- Advanced threat protection integrates malware detection, sandboxing for suspicious files, and connections to cloud-based threat intelligence. The firewall constantly learns about new threats and automatically updates its defenses.
- User identity awareness ties security policies to specific users or groups. Your marketing team might get different access than your developers, regardless of which device or IP address they use.
Additional Capabilities
Modern NGFWs connect to threat intelligence feeds from around the world. When researchers discover a new threat in Asia, your firewall learns about it within minutes.
Many NGFWs now include SD-WAN functionality, helping distributed organizations manage and secure traffic across multiple locations. Cloud-based management consoles let you configure and monitor firewalls from anywhere.
The analytics and reporting features give security teams visibility they never had before. You see which applications consume bandwidth, which users trigger policy violations, and where threats attempt to breach your network.
Real-World Value
Large enterprises accounted for 70% of the NGFW market revenue in 2024, deploying these solutions to handle multi-gigabit traffic inspection without compromising performance. These devices consolidate multiple security functions, reducing the number of products you need to buy, deploy, and manage.
For organizations moving to cloud environments or hybrid landscapes, NGFWs provide consistent security policies across all locations. You protect data the same way whether it lives in your data center or in AWS.
Compliance becomes easier, too. Many regulatory frameworks require specific security controls that NGFWs deliver out of the box.
Comparing Your Options
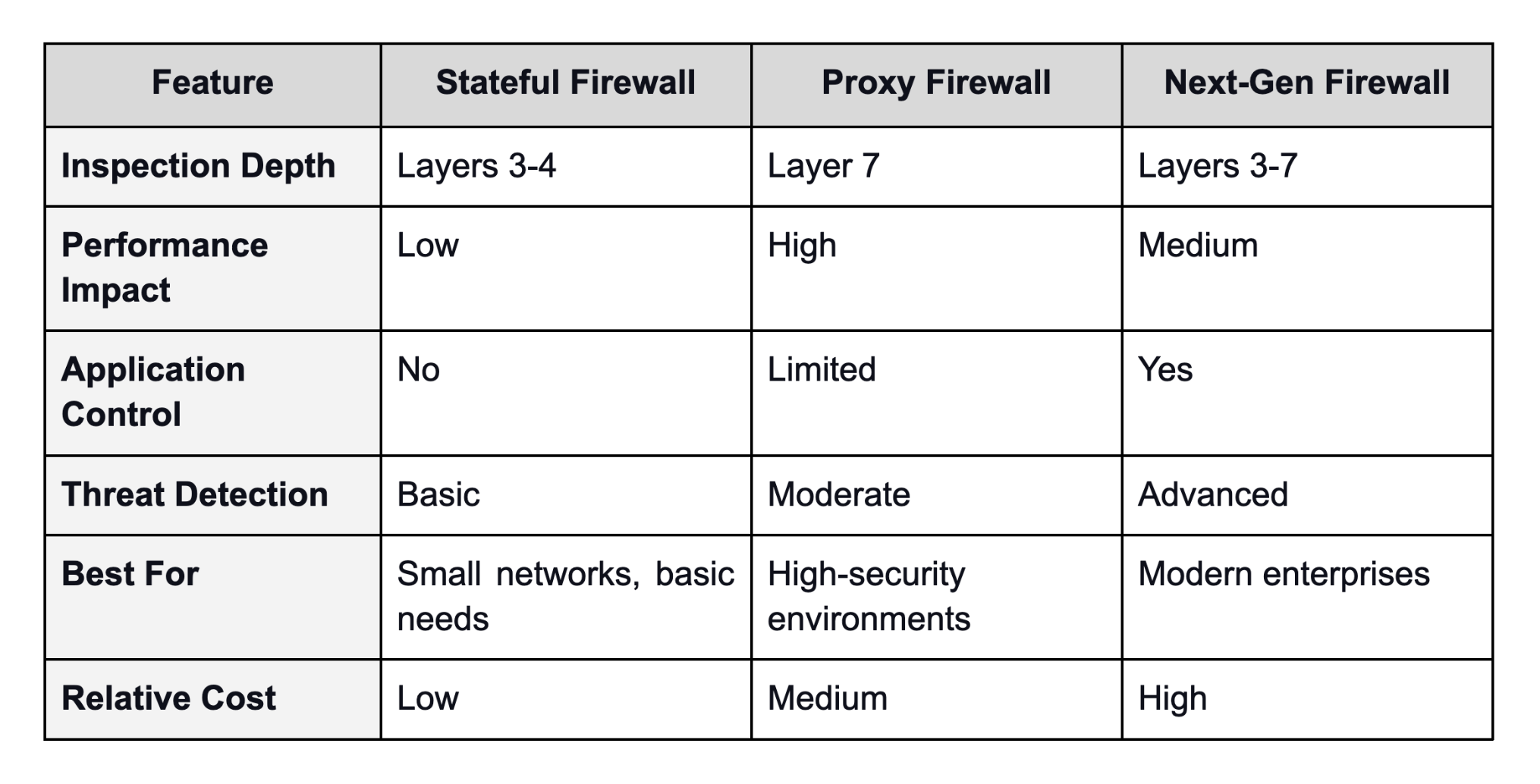
Choosing the Right Firewall
Your organization's size, budget, and risk profile determine which specific or multiple firewall types make the most sense.
- Small businesses with straightforward needs might find stateful firewalls sufficient, especially if they lack IT security expertise. The lower cost and simpler firewall management appeal to resource-constrained teams.
- Mid-sized companies handling sensitive data should consider NGFWs. The investment pays off through better threat prevention and reduced breach risk.
- Large enterprises almost universally deploy NGFWs now. The complexity of modern networks, cloud integration needs, and sophisticated threat landscape make anything less inadequate.
- Industry-specific requirements also significantly matter. Healthcare organizations need HIPAA compliance. Financial institutions face strict data protection mandates. NGFWs deliver the controls and audit trails these regulations demand.
Conclusion
No single firewall type solves every security challenge. Your best defense combines multiple layers of protection, with firewalls forming the foundation.
The trend clearly points toward NGFW adoption. As external threats evolve, basic traffic filtering no longer provides adequate protection. Organizations need the visibility, control, and threat prevention that only next generation firewalls deliver.
Take time to assess your current security posture.
- What threats do you face?
- What data needs protection?
- Where do gaps exist in your defenses?
These questions guide you toward the right firewall choice for your specific situation.
Firewall technology continues to advance as well. Artificial intelligence and machine learning now help firewalls automatically identify zero-day threats and adapt to new attack patterns. The next generation of next-generation firewalls promises even stronger protection.
Whatever you choose, remember that firewalls work best as part of a comprehensive security strategy. They guard the perimeter, but you need defenses throughout your network to truly stay secure.



